Continuous Threat Exposure Management (CTEM) is becoming increasingly important in the field of cybersecurity. As organisations face more sophisticated and frequent cyber threats, there is a growing need to move beyond traditional vulnerability management approaches. CTEM offers a more dynamic and proactive way to identify, assess, and mitigate potential threats, helping organisations stay ahead of attackers and better protect their digital assets.
Knowledge CTEM Framework Explained: The 5 Stages of Continuous Threat Exposure Management
1. What Is CTEM?
Continuous Threat Exposure Management (CTEM) is becoming increasingly important in the field of cybersecurity. As organisations face more sophisticated and frequent cyber threats, there is a growing need to move beyond traditional vulnerability management approaches. CTEM offers a more dynamic and proactive way to identify, assess, and mitigate potential threats, helping organisations stay ahead of attackers and better protect their digital assets.
2. The Five Stages of CTEM
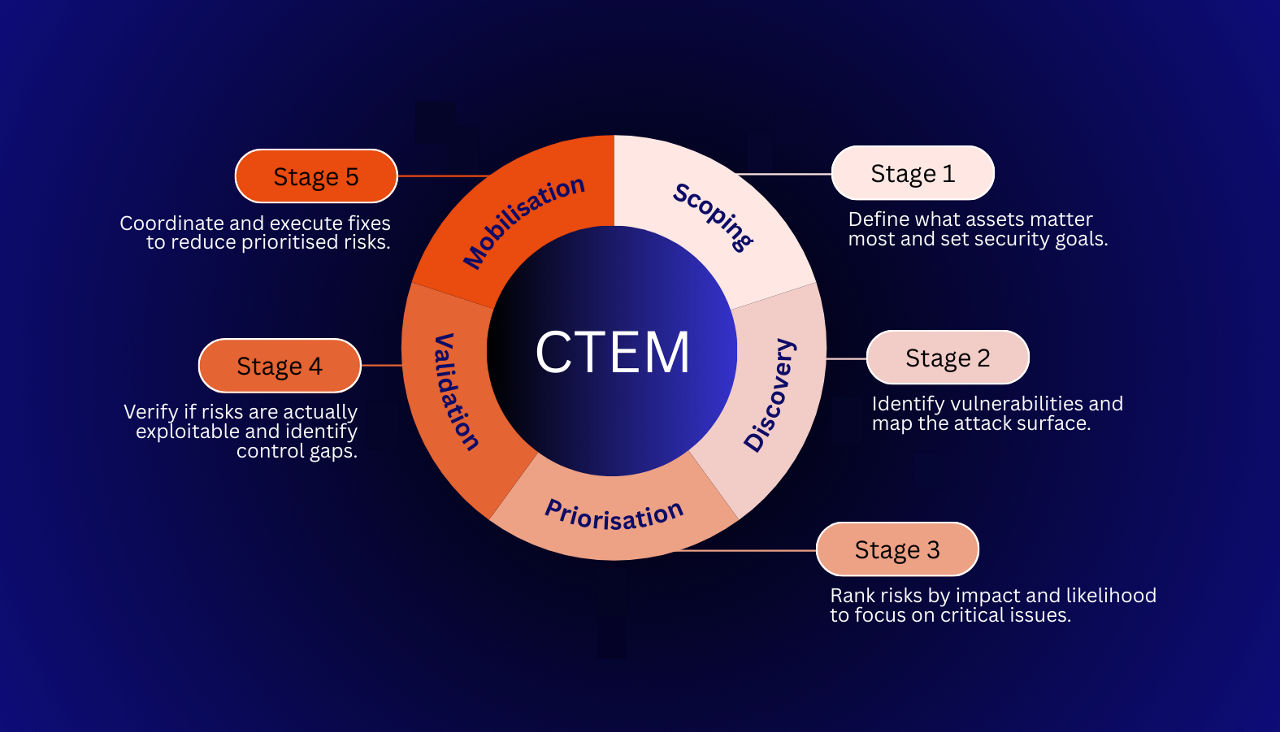
The Continuous Threat Exposure Management (CTEM) process is a comprehensive approach to identifying and reducing an organisation's exposure to cyber threats. It consists of five key steps:
Scoping
Begin by identifying the organisation’s most valuable and sensitive assets, such as customer data, intellectual property, and critical infrastructure. This step also involves mapping out all potential attack surfaces, including networks, applications, and third-party integrations, to understand where threats could emerge.
Discovery
Use automated tools and manual techniques to uncover vulnerabilities, misconfigurations, and exposures throughout the environment. This process helps reveal weaknesses in systems, software, and security policies that could be exploited by attackers.
Prioritisation
Analyse the identified risks by evaluating their potential impact on business operations and the likelihood that they could be exploited. This allows the organisation to focus resources on addressing the most significant threats first.
Validation
Test whether the discovered risks can actually be exploited in real-world scenarios, such as through penetration testing or simulated attacks. This step also assesses the effectiveness of existing security controls and identifies any gaps that need improvement.
Mobilisation
Develop and implement a coordinated response plan to remediate prioritised threats. This includes assigning tasks, deploying fixes or patches, updating security measures, and monitoring progress to ensure that identified risks are effectively mitigated.

By following these five steps, organisations can systematically manage and reduce their exposure to cyber threats.
3. Key Components and Technologies of CTEM
CTEM, or Continuous Threat Exposure Management, relies on several essential components and technologies to be effective. It involves continuous risk assessment and monitoring to identify and evaluate potential threats in real time. The integration of threat intelligence allows organisations to stay informed about emerging risks and vulnerabilities. Automation and the use of artificial intelligence and machine learning (AI/ML) play a significant role in managing exposures efficiently, helping to prioritise and respond to threats quickly. Additionally, CTEM is enhanced by integrating with various security tools such as SIEM (Security Information and Event Management), EASM (External Attack Surface Management), CNAPP (Cloud-Native Application Protection Platform), and others, creating a comprehensive and proactive security environment.
4. Benefits of Adopting CTEM
Adopting CTEM brings several key benefits to organisations:
- Improved visibility and real-time risk awareness: Businesses can continuously understand their security posture.
- Proactive risk reduction and faster remediation: CTEM enables organisations to address threats before they escalate.
- Business alignment and regulatory compliance: CTEM supports meeting legal obligations and maintaining trust.
- Enhanced operational efficiency: Reduces alert fatigue for security teams, helping them focus on the most urgent issues.
5. Challenges and Considerations in CTEM Implementation
Implementing CTEM comes with several challenges and important considerations. Organisations often face resource and skill constraints, making it difficult to allocate the necessary personnel and expertise. Integration complexity can arise as CTEM solutions must work seamlessly with existing systems and processes. Additionally, managing false positives and alert fatigue is crucial to ensure that teams can focus on genuine threats without becoming overwhelmed by unnecessary notifications. Finally, aligning teams and processes is essential for successful implementation, requiring effective communication and collaboration across different departments.
6. How to Deploy a CTEM Program: Best Practices & Measuring
To ensure a successful CTEM program, it's essential to align business objectives with clear scoping and prioritisation, foster cross-team collaboration and ownership, implement automation where it adds value, and maintain continuous improvement through regular feedback. Measuring the effectiveness of your CTEM efforts involves tracking key metrics such as mean time to detect and respond, reduction in critical exposures, elimination of attack paths, and compliance rates, along with reporting to demonstrate ROI.
7. Future Trends in CTEM
As organisations continue to face increasingly sophisticated cyber threats, several key trends are shaping the future of Continuous Threat Exposure Management (CTEM). First, the threat landscape is constantly evolving, with attackers adopting new tactics and techniques to bypass traditional defences. In response, organisations are turning to advanced technologies such as artificial intelligence, automation, and cloud-native tools to enhance their security posture and respond to threats more quickly and effectively. Additionally, there is a growing emphasis on integrating CTEM with Zero Trust principles and other emerging security frameworks, enabling a more holistic and adaptive approach to cybersecurity.
8. Conclusion
In summary, CTEM offers significant value to modern organisations by providing a comprehensive approach to cybersecurity. However, implementing CTEM can be a complex and challenging process, requiring dedicated resources and expertise. Despite these difficulties, CTEM is extremely important for maintaining business efficiency, as it enables organisations to proactively identify and address potential threats, enhancing their overall security posture. Therefore, adopting CTEM is essential for any organisation that wants to stay ahead of evolving cyber risks and ensure robust protection of their digital assets.
Learn more about Our Managed CTEM service, designed to support your organisation with or without an internal cyber security team.
KDDI Europe's Managed CTEM

Cyber Threat Intelligence Report

Related Knowledge Articles