Resources Knowledge

Vulnerability Management vs. Pen Testing: Benefits, Limitations, and Alternative Security Approach

Feb 19, 2026
Knowledge
In today’s rapidly evolving threat landscape, traditional vulnerability management and periodic penetration testing alone are no longer enough to protect your organisation. This guide explores the strengths and limitations of each approach, introduces the concept of Continuous Threat Exposure Management (CTEM), and explains how CTEM delivers continuous, risk-based security—helping you stay ahead of emerging threats and safeguard your digital assets.
What Is a Security Assessment? Explaining Its Purpose, Evaluation Items, and Concrete Process

Jan 14, 2026
Knowledge
This article explains what a security assessment is, from its objectives to specific implementation steps and evaluation items.
CTEM Framework Explained: The 5 Stages of Continuous Threat Exposure Management
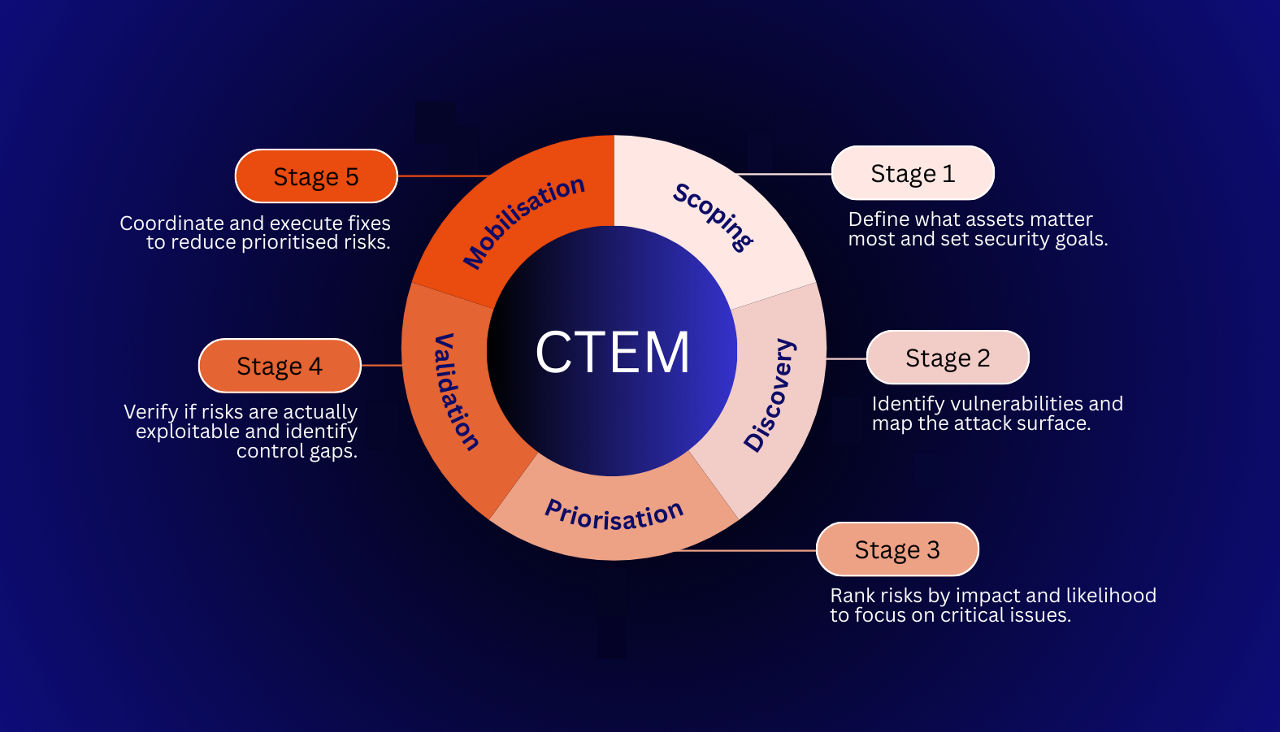
Jan 14, 2026
Knowledge
This article explains what exposure management is, from its objectives to specific implementation steps and evaluation items.
What Are Managed Services? Explaining the Service Features and Benefits That Support Corporate IT Departments

Jan 14, 2026
Knowledge
This article explains what managed services are, from the basics to specific service contents and the benefits of implementation.
What Is Cybersecurity? A Beginner-Friendly Guide to the Basics and Key Countermeasures

Jan 14, 2026
Knowledge
This article explains the basic meaning and importance of cybersecurity, and introduces specific countermeasures that companies and individuals should implement.
What Is a Vulnerability Assessment? Explaining Its Necessity, Costs, and How to Choose a Service

Dec 18, 2025
Knowledge
This article explains the necessity and purpose of vulnerability assessments and how they differ from penetration tests.
What Is a Cyberattack? Main Types, Techniques, and Measures Companies Should Implement Immediately

Dec 18, 2025
Knowledge
This article explains representative types and techniques of cyberattacks, presents cases of cyberattack damage in Japan, and introduces concrete security measures companies should implement right away.
What Are Cloud Security Services? Explaining the Main Types and Key Points for Choosing a Service

Dec 18, 2025
Knowledge
This article introduces information for achieving secure cloud use, including the scopes of responsibility for each type of cloud service and points to check when selecting one.
What Are MDM Security Measures? Explaining Features That Prevent Data Leaks and Key Points for Choosing a Service

Dec 18, 2025
Knowledge
This article clearly explains the specific security features MDM provides and what risks can be prevented by implementing it.
Complete Guide to IAM: Benefits, Security Risks & How It Works

Jun 24, 2025
Knowledge
Learn what Identity and Access Management (IAM) is, its key functions, benefits, threats, and modern IAM solutions to secure enterprise access.
4 Solutions for Visualizing CO2 Emissions! Features and Advantages Explained

May 07, 2025
Knowledge
It is critical to understand the features and benefits of each option and select the one that best meets your company’s needs.
Practical Approaches for Global Carbon Neutrality

Apr 30, 2025
Knowledge
The importance of flexible, site-specific approaches as well as the need for a clear vision from top management.
A Detailed Explanation of the Importance and Benefits of Using IT for Carbon Neutrality

Apr 24, 2025
Knowledge
Achieving carbon neutrality requires visualizing CO2 emissions. Provides a clear introduction to carbon neutrality approaches, especially for those who are new to the field or looking for ways to improve efficiency.
Introducing Carbon Neutrality Initiatives by Region and Country – What Are the Risks of Delayed Action?

Apr 16, 2025
Knowledge
To achieve carbon neutrality, a variety of measures have been put in place. Provides a detailed overview of how various countries are pursuing carbon neutrality.
OT Security – An Essential for Overseas Locations and Factories: Introduction to Risks and Specific Countermeasures

Mar 13, 2025
Knowledge
It is necessary to understand the risks surrounding OT systems and take specific measures to address them.
What is the NIS2 Directive? Introducing its requirements and the need for cyber resilience

Mar 06, 2025
Knowledge
What is the "NIS2 Directive" established by the EU? We provide specific guidelines for enhancing security related to the NIS2 Directive.
Cybersecurity in the Academic Environment – The Threat from Anyone, Anywhere, at Any Time.

Jan 24, 2025
Blog
Cybersecurity in academia is crucial to protect sensitive data, intellectual property, and the wellbeing of students and staff. Dr. Nick Polydorou explores the unique challenges faced by educational institutions and the evolving threats they encounter.
What is ITOC? - IT Operation Centre: 24/7 IT Support, Monitoring, and Incident Management

Oct 25, 2024
Blog
KDDI Europe’s IT Operations Centre (ITOC) offers 24/7 comprehensive IT support, proactive monitoring, and incident management. Located at Telehouse Docklands, ITOC provides expert-certified staff, multi-tiered support, and seamless cloud and network services, helping businesses reduce downtime, cut costs, and focus on growth.
The Role of Security and IT Service Integrators Amidst Growing IT Product Vulnerabilities

Oct 21, 2024
Blog
Experts from KDDI Europe explore the critical role of IT and security service integrators in today’s rapidly evolving digital landscape.
Creating a Society in which Anyone Can Make Their Dreams a Reality, Starting from Japan—KDDI's Launch of "WAKONX (WAKON-CROSS)", a Business Platform for the AI Era

Aug 23, 2024
Knowledge
To speed up Japan's digitalization, KDDI has introduced a new business platform centered on collaboration and competition.
What is Zero Trust (Security Measures for IoT) at Overseas Offices? Points to Realize

Jun 27, 2024
Knowledge
What is security for IoT devices? Describing effective security measures
What is Endpoint Security? Explaining its Importance in the Zero Trust Model and Best Practice at Overseas Offices

Jun 26, 2024
Knowledge
What is security in teleworking? Describing effective security measures for mobile devices
On What Threats Should We Focus in Overseas Offices? Explaining the Idea of Zero Trust

Jun 19, 2024
Knowledge
What threats can we prevent by zero trust? Illustrating increasingly diversifying and complex cyber threats in a comprehensible way
What are the Components of Zero Trust? Explaining the Best Security Technology Required for the IT Environment that is Becoming Increasingly Diverse at Overseas Offices

Jun 18, 2024
Knowledge
What is the concept of security that overseas offices are looking for? A comprehensive look at the latest trends in technology, including zero trust components and the components of zero-trust architecture.
How do you strengthen IT governance at overseas locations? Expanding KDDI networks across the globe to comprehensively support the IT governance in and outside Japan

May 22, 2024
Knowledge
Introducing security challenges and countermeasures at overseas locations
The process of establishing, relocating, and renovating offices overseas

May 16, 2024
Knowledge
Utilizing one-stop services is an effective option for establishing, relocating, or renovating offices at overseas locations. In this article, we will explain the points for selecting a contractor to smoothly proceed with office relocation, new market entry or corporate office renovation overseas, as well as the importance of a well-designed office IT setup.
Key information security measures when smart office enabling overseas locations

May 09, 2024
Knowledge
What are the security risks associated with smart offices? Explaining four strategies to reduce risk
Overview of business reviews and other measures for creating a smart office

Apr 25, 2024
Knowledge
What are the important business reviews for smart office transformation at overseas locations, and how can tools be used to assist?
What is ABW, a new way of working? Introducing its merits and the necessary initiatives for its implementation

Apr 15, 2024
Knowledge
Aiming for the optimization of the activity-based work environment. Explaining the key points when adopting ABW at overseas locations.






