Cybersecurity risk management helps organisations protect their digital assets by identifying, assessing, and reducing potential threats. A key part of this process is addressing vulnerabilities before attackers can exploit them. Vulnerability management is an ongoing process for detecting and fixing security flaws, while vulnerability assessment provides a focused evaluation to identify breadth of weaknesses. Alongside penetration testing, which provides in-depth analysis of weakness, these practices are often combined as VAPT (Vulnerability Assessment and Penetration Testing) to form the foundation of an effective cybersecurity strategy.
Knowledge Vulnerability Management vs. Pen Testing: Benefits, Limitations, and Alternative Security Approach
1. What is Vulnerability Management?
Definition and key components
Vulnerability Management is the systematic process organisations use to identify, assess, prioritise, and remediate security vulnerabilities in their IT environments. Key components include asset discovery, vulnerability scanning, risk assessment, remediation, and reporting. This approach was once considered modern, but now it is seen as limited due to its focus on known vulnerabilities and predictable processes.
Tools and technologies commonly used
Common tools include vulnerability scanners, asset management platforms, and reporting dashboards. These tools automate the detection of known vulnerabilities but often unable to detect misconfigurations, business logic flaws, or new attack vectors, making them less effective in the face of evolving threats.
Role in compliance and foundational security
Vulnerability management has played a foundational role in helping organszations meet compliance requirements and establish basic security hygiene. However, as compliance standards and attacker techniques advance, relying solely on traditional vulnerability management is no longer sufficient for robust security.
Benefits of Vulnerability Management
1. Identification of known weaknesses |
It provides on demand detection of known vulnerabilities, helping organisations stay ahead of threats that have already been documented. However, this benefit is less significant as attackers increasingly target unknown or unaddressed weaknesses. |
2. Automated, scalable, and repeatable |
The automated nature of vulnerability management allows organisations to scale their efforts and maintain consistent processes. Yet automation is limited to what is already known and cannot easily adapt to new or sophisticated threats. |
3. Supports regulatory and compliance requirements |
Vulnerability management helps organisations meet industry regulations and standards. Still, compliance alone does not guarantee security, and attackers often exploit gaps not covered by compliance checks. |
4. Enables risk reduction |
By addressing vulnerabilities, organisations can reduce their risk exposure. However, this reduction is limited to known risks, and unknown or unprioritised issues may persist. |
Limitations of Vulnerability Management
1. Focus on known CVEs and technical flaws |
Traditional vulnerability management centers around known CVEs and technical issues, missing new or unique attack methods. This narrow focus makes it less effective as attackers innovate beyond publicly disclosed vulnerabilities. |
2. Can overlook misconfigurations and business logic issues |
Many tools do not detect configuration errors or business logic flaws, which are increasingly exploited by attackers. This limitation contributes to the perception that vulnerability management is an aging solution. |
3. May generate long lists without clear prioritisation |
The process often results in extensive lists of vulnerabilities, making it difficult for organisations to prioritise and address the most critical issues. This can lead to inefficiencies and unresolved risks. |
4. Lacks exploitability validation |
Vulnerability management tools usually do not validate whether a vulnerability can actually be exploited in a given environment, leading to wasted effort on low-risk or irrelevant issues. |
Vulnerability Management is increasingly viewed as an aging solution because it primarily addresses known vulnerabilities and technical flaws. As cyber threats become more sophisticated, attackers often exploit unknown vulnerabilities, misconfigurations, or business logic errors that traditional vulnerability management tools may not detect. Additionally, the approach can result in overwhelming lists of issues without effective prioritisation or validation of which vulnerabilities are actually exploitable, making it less effective for modern security needs. Organisations are seeking more advanced solutions that incorporate threat intelligence, exploitability analysis, and risk-based prioritisation to address these gaps.
2. What is Penetration Testing?
Definition and objectives
Penetration testing, or pen testing, is a security assessment method where professionals simulate cyberattacks on systems, networks, or applications. The main objectives are to identify vulnerabilities, assess potential risks, and help organisations strengthen their security posture.
Types of pen tests (internal, external, web application, etc.)
There are several types of penetration tests, including internal tests that examine threats from within the organisation, external tests that focus on threats from outside, and web application tests that target vulnerabilities specific to web-based applications. Each type addresses different attack vectors and scenarios.
The human element: rules of engagement and ethical considerations
The human element is crucial in pen testing. Rules of engagement must be established to ensure testing is ethical, legal, and does not disrupt business operations. Testers need to consider privacy, data protection, and organisational policies throughout the process.
How pen testing differs from automated scanning
Penetration testing differs from automated scanning because it involves manual techniques and creative approaches that mimic real attackers. Automated tools can identify known vulnerabilities, but pen testers can discover complex attack paths and vulnerabilities that automated tools might miss.
Benefits of Penetration Testing
1. Simulates real-world attacker tactics |
By simulating real-world attacker tactics, pen testing gives organisations a realistic view of their security weaknesses and how they might be exploited. |
2. Uncovers complex attack paths and chained vulnerabilities |
Pen testing uncovers complex and chained vlunerabilities that automated scan is unable to find but often used by attackers to exploit target systems |
3. Provides actionable insights for remediation |
The findings from pen testing provide actionable insights that help organisations prioritise and address the most critical vulnerabilities. |
4. Validates the effectiveness of existing controls |
Pen testing also validates the effectiveness of existing security controls, ensuring they work as intended against real threats. |
Limitations of Penetration Testing
1. Point-in-time Assessment, Not Continuous |
Vulnerability management typically provides a snapshot of security at a specific moment. This means that new vulnerabilities discovered after the assessment may go unnoticed until the next scheduled review, leaving potential gaps in protection. |
2. Resource-Intensive and Potentially Disruptive |
Conducting vulnerability assessments requires significant time, skilled personnel, and technical resources. These assessments may also temporarily disrupt normal business operations, as systems must be scanned and tested, sometimes affecting performance or availability. |
3. Dependent on Tester Skill and Defined Scope |
The effectiveness of vulnerability management depends heavily on the expertise of the testers and the scope of the assessment. If the scope is too narrow or testers lack experience, critical vulnerabilities might remain undetected, reducing the overall security of the organisation. |
4. May Miss Exposures Outside the Engagement Window |
Since vulnerability assessments are usually scheduled events, any security issues that arise between assessments may not be identified or addressed promptly. This creates windows of exposure where threats can go unnoticed until the next review. |
3. When to Use Each Approach
Scenarios Best Suited for Vulnerability Management
Vulnerability management is ideal for organisations seeking regular monitoring and regular assessment of their systems. It helps identify known weaknesses, prioritise remediation, and maintain a proactive security posture. This approach is especially useful in environments with frequent changes or where compliance requires ongoing oversight.
Scenarios Where Pen Testing Is Essential
Penetration testing is crucial when you need to simulate real-world attack scenarios to uncover hidden vulnerabilities that automated tools might miss. It is particularly important before launching new applications, after significant infrastructure changes, or to meet regulatory requirements that demand comprehensive security validation.
The Value of Combining Both for Layered Security
Integrating vulnerability management and penetration testing offers a robust defense strategy. While vulnerability management provides insight into potential risks, pen testing validates the effectiveness of security controls and uncovers complex attack paths. Together, they create a layered approach that enhances overall protection.
How Frequency and Timing Impact Effectiveness
The effectiveness of these security measures depends on how often and when they are performed. Regular vulnerability scans ensure ongoing risk awareness, while periodic pen tests, scheduled after major updates or at set intervals, help assess the evolving threat landscape. Balancing frequency and timing ensures that security defenses remain strong and up to date.
4. Alternatives and Enhancements: Beyond Traditional Methods
Traditional security methods often can't keep up with fast-changing threats. They may only assess risks occasionally, leaving gaps in protection, and often lack full visibility or up-to-date risk prioritisation. This leads to slower detection, inefficient resource use, and higher risk of attacks. A new solution is needed—one that offers continuous, proactive, and intelligence-driven security management.
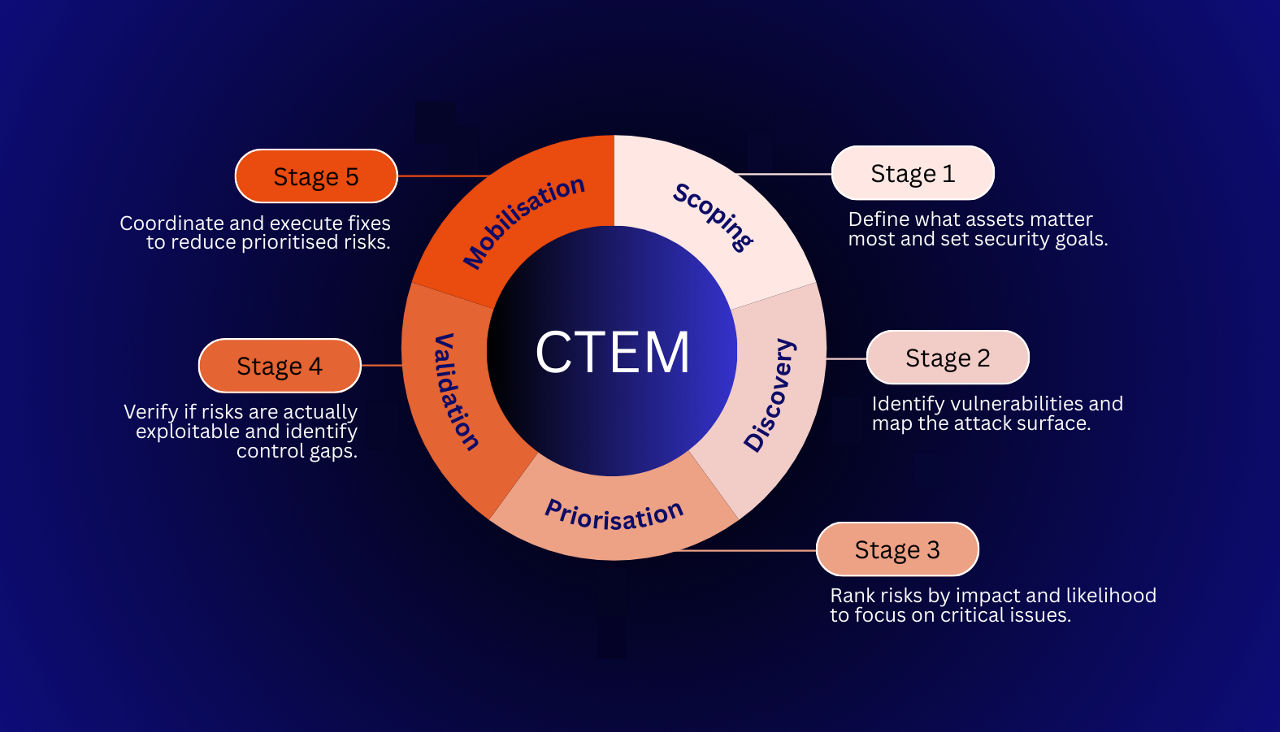
Continuous Threat Exposure Management (CTEM)
Continuous Threat Exposure Management (CTEM) is a proactive approach that helps organisations identify, assess, and address security vulnerabilities on an ongoing basis. By continuously monitoring their digital environments, businesses can stay ahead of potential threats and reduce the risk of cyberattacks.
Breach and Attack Simulation (BAS) and Attack Surface Management (ASM)
Breach and Attack Simulation (BAS) tools allow organisations to simulate real-world cyberattacks in a controlled environment, helping them evaluate their security posture and identify weaknesses before attackers do. Attack Surface Management (ASM) involves continuously discovering and monitoring all digital assets exposed to the internet, ensuring that security teams are aware of potential entry points for attackers.
Integrating threat intelligence and risk-based prioritisation
Integrating threat intelligence into security operations enables organisations to make informed decisions based on the latest information about emerging threats. Risk-based prioritisation helps security teams focus their efforts on addressing the most critical vulnerabilities first, optimizing resource allocation and improving overall defense effectiveness.
5. Conclusion
How to Enhances Security and Fills the Gaps
Traditional vulnerability management and penetration testing each play a vital role in cybersecurity, but both have limitations when used alone. Vulnerability management focuses on known issues, and pen testing simulates real attacks to uncover hidden risks—yet both may miss emerging threats and lack continuous coverage.
Continuous Threat Exposure Management (CTEM) addresses these gaps by providing ongoing, risk-based visibility and prioritisation, ensuring organisations can identify and respond to new threats as they arise.
Recommended Next Steps
Review your current vulnerability management and pen testing processes to spot any gaps or areas for improvement such as insufficient frequency, inefficient human resource utilisations, invisible attack surfaces.
If you find any gaps, consider exploring additional security tools or approaches that offer continuous monitoring and risk-based prioritisation security services.
If you want to learn more about CTEM, check out our blog below. Or if you’d like help reviewing your security posture, just contact us using the form below—we’re here to help.
KDDI Europe's Managed CTEM

Would you like to review the security posure?

Related Knowledge Articles